My interview with Jake from Black Tower Radio. During the interview I talk about my experience at CIA and the events that led to me becoming a CIA Whistleblower. Highlights include how CIA psychiatrist Mary Newman blew my cover, the incompetence of CIA’s Office of Security and CIA’s poor OPSEC posture. I discuss why its surprising Wikileaks Vault 7 leak didn’t happen sooner given CIA’s incompetence.
Tag: Counterespionage
Wikileaks: A Spy Agency for the 21st Century
We are, in a sense, a pure expression of what the media should be: an intelligence agency of the people, casting pearls before swine. –Julian Assange
From its humble beginnings as a neutral worldwide watchdog in 2006, Wikileaks has successfully transformed itself into a transnational spy service, turning the traditional spy agency model on its head. The nation-state spy agency is no longer the greatest threat to a state’s secrets. Autonomous, unaccountable agencies, like Wikileaks, can arguably do as much or more damage to a nation’s security. This is not a condemnation of Wikileaks; its founder, Julian Assange, is not a US citizen and owes no allegiance to the US or its constitutional laws. At the same time, Americans must recognize that Wikileaks is not a benign whistle-blowing organization acting on their behalf.
Since its founding, Wikileaks has billed itself as a non-profit media organization, seeking to shine light on abuses of power. Wikileaks argues that when government and other officials know their wrongdoing may be outed, they are less likely to engage in corrupt activity.
WikiLeaks is a not-for-profit media organisation. Our goal is to bring important news and information to the public… The power of principled leaking to call governments, corporations and institutions to account is amply demonstrated through recent history. The public scrutiny of otherwise unaccountable and secretive institutions forces them to consider the ethical implications of their actions. Which official will chance a secret, corrupt transaction when the public is likely to find out? What repressive plan will be carried out when it is revealed to the citizenry, not just of its own country, but the world? When the risks of embarrassment and discovery increase, the tables are turned against conspiracy, corruption, exploitation and oppression. Open government answers injustice rather than causing it. Open government exposes and undoes corruption. Open governance is the most effective method of promoting good governance1.
Wikileaks’ mission sounds noble but peeling back the layers reveals Wikileaks operates more like a spy agency than a media outlet. Wikileaks does not function as the people’s intelligence agency that Assange described in the NewStatesman in 20112. Assange has his own priorities, his own goals, his own mission, and empowering the American people is not one of them. Upon closer examination it becomes clear that Wikileaks views the United States as its primary enemy. The goal appears to be a strong attempt at undermining US hegemony. In a January 2, 2007 email, Assange explains Wikileaks potential, “…Wikileaks can advance the political/governance aspects of these developments by several years…the least of which is total annihilation of the current US regime and any other regime that holds its authority through mendacity alone.3” In a bid to diminish US power, Wikileaks engages in many of the same activities as a traditional nation-state spy agency, including the recruitment of spies; the collection, exploitation and analysis of secret information; and psychological operations, in support of its goals.
I. Recruitment
Wikileaks recruits sources, known in the spy world as assets or agents, much like a nation-state intelligence service would. Unlike traditional intelligence services, Wikileaks does not have access to dossiers on diplomats it can wine and dine in hopes of turning them into spies. Instead, Wikileaks uses the internet to advertise its mission, making it easy for leakers to find them. Wikileaks operates based on digital walk-ins, similar to how CIA relied on walk-ins for its intelligence gathering on the Soviet Union during the Cold War4. In “The Great Game,” former CIA Inspector General Frederick P. Hitz describes a walk-in as, “…the practice of a volunteer spy or defector literally walking into an embassy or official installation and offering his services to the Marine on duty5.” Assange has remade the walk-in for the 21st century. On March 13, 2017, Wikileaks appeared to troll the CIA with a Tweet asking if the CIA’s ad for internships was a “whistleblower” opportunity.
CIA advertises internships. Whistleblowing opportunity? https://t.co/6JPCopFkEi
— WikiLeaks (@wikileaks) March 13, 2017
Although the above tweet was framed as a joke, it was a recruitment pitch. A Whistleblower happens upon corruption, s/he does not go to work for an organization with plans to abscond with secret documents, under the assumption the organization is corrupt. A week later, on March 20, 2017, Wikileaks tweeted a more direct pitch to would be digital walk-ins.
https://twitter.com/wikileaks/status/843618457874784256
A person entering on duty at CIA with the goal of “exposing abuses” for Wikileaks would be the equivalent of a mole or penetration agent. The dictionary of espionage defines a mole or penetration agent as, “a person who’s loyalty lies with the rival power but who joins another cause for duty purposes6.” Wikileaks is trying to recruit people to penetrate the Intelligence Community with plans to steal classified information. Wikileaks calls it whistleblowing because that makes its operations more palatable to the public. Make no mistake, Wikileaks’ goal is recruiting spies, specifically American spies, not Whistleblowers.
II. Collection, exploitation and analysis of secret information
Like nation-state intelligence agencies, Wikileaks collects, exploits and analyzes the secret information it receives. If you visit Wikileaks.org, you will find commentary and analysis alongside the documents it publishes. Wikileaks’ most explosive stories come from secret information about the US. Wikileaks maintains collection priorities, just as nation-state intelligence services do. Although Wikileaks portrays itself as exposing corrupt and oppressive regimes worldwide, it is clear that collecting against the US national security apparatus is Wikileaks top priority. By Wikileaks’ own account, the majority of its “greatest hits” over the past decade have been about the US. The list ends with the Democratic National Committee leak in 2016. One can conclude if the list were compiled today, Vault 7 would make the top 10.
[urlpreviewbox url=”https://wikileaks.org/10years/global.html”/]
Notwithstanding the similarities between Wikileaks and traditional intelligence agencies, Wikileaks appears to have no interest in hoarding secrets to advance its interests, at least not American secrets. Instead, Wikileaks places the secrets it obtains in the public domain, arguably doing more damage to national security than traditional spy agencies operating against the US. One could argue that Wikileaks is not actively collecting against the US, that Wikileaks publishes the information it receives, and the majority of leaked information just happens to come from the US. Is it believable that only the US national security community has a problem with leaks?
Is it believable that there are no leaks within Russian, Chinese or other intelligence services or that these services are not engaged in corrupt behavior? Clearly the answer to these questions is no; which raises the question, why is a majority of the information Wikileaks releases about the US? Is it possible Wikileaks deliberately withholds information on some countries? Some have asserted Wikileaks is a front for Russian intelligence, that its releases advance Russian interests, but the publicly available evidence is inconclusive. Although the Intelligence Community has established that Russian intelligence distributed hacked emails from the Democratic National Committee to Wikileaks and other media outlets during the 2016 presidential election, there is no publicly available evidence suggesting Wikileaks obtained the Vault 7 or other US leaks from Russia7. What is clear is Wikileaks has an anti-American agenda and its collection priorities reflect this agenda.
III. Psychological Operations
The purpose of propaganda is to convey an ideology to an audience with a related objective. Whether it is a government agency attempting to instill a massive wave of patriotism in a national audience to support a war effort, a terrorist network enlisting followers in a jihad, a military leader trying to frighten the enemy by exaggerating the strength of its army, a corporation pursuing a credible image to maintain its legitimacy among its clientele, or a company seeking to malign a rival to deter competition for its product, a careful and predetermined plan of prefabricated symbol manipulation is used to communicate an objective to an audience. The objective is to modify the attitudes, the behavior, or both of an audience8.
Wikileaks is active on social media with official and non-official accounts on websites such as Twitter and Reddit promoting its mission. Wikileaks never releases documents without comment, rather Wikileaks seeks to shape public opinion. Assange employs a vast network to accomplish his targeted propaganda goals. At an October 4, 2016 press conference in Berlin, Assange announced the formation of a “task force” to combat misinformation about Wikileaks. Assange explained, “We have engaged in a new project; to recruit people across the world to defend our publications.” Assange’s army will defend Wikileaks perspective, the goal is not objectivity.
[urlpreviewbox url=”https://motherboard.vice.com/en_us/article/WikiLeaks-is-making-a-twitter-army-to-fight-against-misinformation”/]
Are your devices compromised by the CIA? WikiLeaks Research Community project aims to find out https://t.co/F0ASfxxz2Q #Vault7
— WikiLeaks (@wikileaks) March 20, 2017
There was little debate about the legality of CIA’s operations or whether CIA’s conduct was standard operating procedure for sophisticated intelligence services worldwide. Vault 7 was presented as a rogue program, unique to CIA, which had put the world in danger. While this debate benefited Assange’s and Wikileaks’ agenda, it did little to help the public. If CIA’s cyber weapons are as dangerous as Wikileaks has characterized, should we not be concerned about other nations possessing similar weapons? The US is not the only country engaged in espionage and certainly other countries have developed cyber weapons as well. Indeed, who is to say China, Russia, or another country’s intelligence services do not have more advanced cyber weapons than CIA? These questions rarely surfaced because Wikileaks has a robust and effective PSYOP capability.
Wikileaks PSYOP prowess can also be measured by one of its biggest coups, gaining the support of the President of the United States, Donald Trump. During the 2016 campaign, President Trump repeatedly praised the spy service, some memorable quotes include:
- “Wikileaks is amazing” (10/11/2016)
- “Wikileaks. I love Wikileaks” (10/10/2016)
- “I’ll tell you this Wikileaks stuff is unbelievable…you gotta read it.” (10/12/2016)
- “You hear this? Wikileaks. Big stuff but the press does not report it” (10/12/2016)
- “The sad part is we don’t talk about Wikileaks because it’s incredible.” (10/13/2016)
- “Wikileaks came out with lots of really unbelievable things” (10/15/2016)
- “We’ve learned so much from Wikileaks” (10/20/2016)
- “We love Wikileaks. Wikileaks.” (10/21/2016)
President Trump sided with Wikileaks over the Intelligence Community regarding Russian interference in the 2016 election, tweeting out Assange’s assessment of who hacked the Democrat’s accounts.
Julian Assange said "a 14 year old could have hacked Podesta" – why was DNC so careless? Also said Russians did not give him the info!
— Donald J. Trump (@realDonaldTrump) January 4, 2017

IV. Conclusion
CIA’s Millennials are not to blame for the Wikileaks Vault 7 leak
In an overt display of ageism, during an interview with BBC on March 8, 2017, ex-CIA Director Michael Hayden blamed millennials for the Wikileaks Vault 7 leak. After admitting he had no special knowledge of the Vault 7 leaks, Hayden launched into a discriminatory tirade against millenials, saying, “In order to do this kind of stuff we have to recruit from a certain demographic. I don’t mean to judge them at all, but this group of millennials and related groups simply have different understandings of the words loyalty, secrecy and transparency than certainly my generation did.”
Hayden conveniently ignored the legions of traitors from his own generation, while slandering the Intelligence Community’s youngest generation. Notable turncoats from Hayden’s generation include:
[urlpreviewbox url=”http://spymuseum.com/aldrich-ames/”/]
[urlpreviewbox url=”http://spymuseum.com/harold-nicholson/”/]
[urlpreviewbox url=”http://spymuseum.com/robert-hanssen/”/]
[urlpreviewbox url=”http://spymuseum.com/earl-pitts/”/]
[urlpreviewbox url=”http://spymuseum.com/ronald-pelton/”/]
[urlpreviewbox url=”http://spymuseum.com/jonathan-pollard/”/]
If we are going to group people by generation, why not race? Besides being part of Hayden’s generation, what demographic group do these spies belong to? They are all White men. Statistically, White men are more likely to commit treason than any other demographic in the Intelligence Community. Why did Hayden fail to point this out during his BBC interview? Edward Snowden and Chelsea Manning, the two leakers Hayden cites as evidence millennials are untrustworthy, were both White men when they unlawfully disclosed classified information.
The problem with Hayden’s analysis of millennials is that once we begin categorizing demographic groups as security threats, where does it end? How does one determine whether race or age is the decisive variable? An intellectually lazy person could just as easily say, White men have a problem with loyalty, secrecy and transparency. In fact, we could insert any demographic and make similarly sweeping generalizations.
Character is not determined by age, similarly it is not determined by race, gender, color, sexual preference, disability status or genetic information. Although specific motives may differ, a lack of character is what drives someone to betray their country and the oath they took to safeguard the nation’s secrets, membership in a particular demographic group is not the deciding factor. Why do White men account for the largest number of spies within the Intelligence Community? Because they are overrepresented in positions with access to the nation’s most sensitive secrets. The Intelligence Community remains the least diverse of all US government agencies.
[urlpreviewbox url=”https://www.washingtonpost.com/news/powerpost/wp/2016/06/13/intelligence-community-doesnt-look-like-either-federal-or-overall-workforces/?utm_term=.fc81561c29e6″/]
Just as we should not assume all White men are disloyal based on the actions of a few, we should not assume all millenials are Edward Snodwens or Chelsea Mannings lying in wait. Stereotyping is not going to keep the Intelligence Community’s secrets safe, and Hayden was reckless to traffick in them. Hayden and Intelligence Community leaders must remember, correlation does not imply causation. The only difference between Hayden’s generation and millennials: the technology has changed and CIA’s Office of Security is still operating from its 1947 model.
[urlpreviewbox url=”https://www.cia.gov/news-information/blog/2014/histint-the-national-security-act-of-1947.html”/]
CIA’s Office of Security is charged with protecting the Agency’s secrets, Wikileaks Vault 7 is the lastest example of its failure to fulfill its mission. Unforntunately, the Office of Security often escapes blame after a major security breach, with congressional investigations most often focusing on the Directorate of the CIA Officer responsible for the espionage. This approach ignores the integral role the Office of Security plays in personnel security.
- The Office of Security is responsible for ensuring Agency contractors follow proper procedures.
- The Office of Security decides who gets and keeps a security clearance.
- The Office of Security conducts background checks and polygraph exams.
- The Office of Security is responsible for maintaining control of classified documents.
- The Office of Security is also tasked with preventing espionage, arguably its most important responsibility.
What is bewildering is that the Office of Security is rarely investigted when CIA suffers a spectacular breakdown in security as it did with Wikileaks Vault 7. What is most disturbing is instead of exercising oversight, Congress often grants more authority to the Office of Security following a counterespionage disaster.
This lack of accountability has allowed the Office of Security’s ineffective culture to become fossilized. In the spy-world, bureaucratic inertia is potentially deadly, but the Office of Security provokes so much fear among the CIA workforce, most do not dare criticize it. CIA employees know criticizing the Office of Security can equal career suicide, given the specter of having their security clearance revoked, most try to fly under the radar of the Agency’s tyrannical Security Officers. Congress and Intelligence Community leadership refuse to hold the Office of Security accountable, thus it has no incentive to change, innovate, or even operate in an ethical manner.
According to Ronald Kessler in his book, “Inside the CIA,” former CIA Director William Webster found the Office of Security more difficult to deal with than any other office at the Agency.
He found it to be still operating in the dark ages and the most resistant to change. Sometimes Websters’ aides felt that perphaps the Office of Security considered Webster to be a security risk.
A former Office of Security official confirmed Webster’s account to Kessler, adding:
Their attitude is, this is the way we do things, and we aren’t going to change.
To date, nobody has forced the Office of Security’s hand; nobody with the authority to do so has had the moral courage to stand up to the Office of Security and demand change.
The usual talking heads are making the rounds in print and on television trying to shift blame from CIA to third parties for the security breach that led to WikiLeaks obtaining CIA’s entire hacking arsenal. Don’t be distracted by CIA’s attempts at damage control via Hayden or anyone else, the blame lies solely with the Agency’s broken security apparatus. CIA was criminally negligent in its failure to secure highly classified information, and in order to move forward in a productive way, CIA must take full responsibility for the loss. The first step towards meaningful and sustainable change is to acknowledge there is a problem, in the same way a drug abuser must admit s/he has a problem before recovery can begin. CIA must take the first step by admitting the problem, only then will it be able to effectively address the structural problems that created the perfect storm for this historic loss of classified information.
Wikileaks Vault 7: CIA’s Operations Security Apocalypse
The Agency is paying for its unwillingness to take OPSEC seriously
A nation can survive its fools, and even the ambitious. But it cannot survive treason from within. An enemy at the gates is less formidable, for he is known and carries his banner openly. But the traitor moves amongst those within the gate freely, his sly whispers rustling through all the alleys, heard in the very halls of government itself. For the traitor appears not a traitor; he speaks in accents familiar to his victims, and he wears their face and their arguments, he appeals to the baseness that lies deep in the hearts of all men. He rots the soul of a nation, he works secretly and unknown in the night to undermine the pillars of the city, he infects the body politic so that it can no longer resist. A murderer is less to fear. — Marcus Tullius Cicero
Unlike most of the public, my initial reaction to Wikileaks release of documents detailing CIA’s cyber-spying was not one of shock at CIA’s vast hacking capabilities. As a former intelligence officer, I was not surprised by the breadth of CIA’s capabilities, what shocked me, was the depth of CIA’s counterespionage incompetence. I was aware of existing gaps in CIA’s Operations Security (OPSEC), but I had never dreamt CIA security was so broken we would witness a counterespionage failure of this scope, one that places Edward Snowden in the Junior Varsity league of intelligence leaks, and renders Chelsea Manning almost inconsequential by comparison. But on March 7, 2017, the unimaginable happened as Wikileaks began publishing details of CIA’s cyber-spying capabilities, a stunning acquisition by Julian Assange.
RELEASE: Vault 7 Part 1 "Year Zero": Inside the CIA's global hacking force https://t.co/h5wzfrReyy pic.twitter.com/N2lxyHH9jp
— WikiLeaks (@wikileaks) March 7, 2017
It would be misleading to say I did not see the potential for a counterespionage disaster of biblical proportions brewing at CIA, in part because as a CIA Whistleblower, I have unintentionally become part of CIA’s failed OPSEC narrative. I have witnessed CIA treat OPSEC with a disdain that is remarkable for an agency considered paranoid about OPSEC by many in the Intelligence Community, who are on the outside looking in. I was once one of those people looking in at CIA from the outside, as an analyst at the Defense Intelligence Agency (DIA), from 2006 until I transferred to CIA in the summer of 2009. DIA taught me OPSEC. From my initial training in DIA’s “Tomorrow’s Intelligence Professionals” to my deployment to Iraq with The Joint Special Operations Command, I learned good OPSEC could mean the difference between life and death. I also witnessed what I perceived to be the paranoia of CIA analysts, who refused to share intelligence with DIA and others in military intelligence. I mistakenly thought the behavior of CIA analysts was indicative of CIA’s strong OPSEC culture. I naively assumed CIA’s OPSEC posture was much stronger than what we had at DIA and in the military community. At the time, I had no idea CIA took a laxer approach to OPSEC than DIA. I did not understand that the pushback I had experienced during my deployment to Iraq was simply bureaucratic game playing by CIA analysts who cared more about preserving their diminishing position in the intelligence community than seriously countering terrorism.
I would not understand CIA’s contempt for OPSEC until I arrived at Langley on July 5, 2009 as a Clandestine Service Trainee. I would not grasp the extent of CIA’s non-existent OPSEC posture until I found myself in the middle of a CIA Security debacle barely three months later, beginning in late-October of the same year. After a fellow Clandestine Service Trainee made spurious allegations against me, CIA’s Office of Security began treating me as a mole within the CIA’s ranks. The ineptness of CIA’s Office of Security in my case illustrates why CIA has been unable to detect the real moles burrowing their way into the Agency’s most closely guarded programs, expressly, CIA’s biases lead it to focus on the wrong employees as potential threats. To make a long story short, in October 2009, CIA committed me against my will to Dominion Hospital in Falls Church, Virginia. At Dominion, psychiatrists acting on behalf of CIA’s Office of Medical Services, detained me, interrogated me, and attempted to force me to take anti-psychotic drugs, all in the name of proving I was a threat to national security whose Top Secret Clearance should be revoked.
There was one significant problem with CIA’s conduct: I was an undercover officer, and CIA Security and Medical Officers leaked highly classified information in zealous pursuit of their objective — proving I was a national security threat. These officers openly and proudly refused to follow basic OPSEC procedures, calling me paranoid and mocking me when I resisted their brazen disregard for protecting classified information. They insisted I speak to them on unsecured phone lines and they transmitted classified materials about my case via unsecured mail, email and fax. CIA Security and Medical Officers revealed my classified identity to Dominion Hospital Staff and Washington, DC police officers, in violation of the Intelligence Identities Protection Act of 1982. The ultimate shock to my OPSEC sensibilities would come when CIA psychiatrist Mary Newman along with psychiatrists Richard Roth and Gary Litovitz at Dominion Hospital, labeled me psychotic, citing my unwillingness to compromise on basic OPSEC procedures as a symptom corroborating the false diagnosis they gave me. I was appalled and continue to be appalled by the ignorance CIA employees have displayed of basic OPSEC. At the time, I was fighting CIA’s unrelenting attacks on my civil rights, trying to keep my head above water, and could not invest much time or effort in confronting the issue.

CIA’s Special Activities Staff in the Office of Security failed to remove the confidential classification marking (C) on a letter mailed to me while I was still undercover in 2010. The 20505 zip code identifies the letter as coming from CIA. This was just one of many OPSEC failures by CIA Security in my case.
Almost eight years later and CIA’s OPSEC posture has not changed. A little over two years ago, CIA Security informed me that I had classified material at my residence in Spain, but refused to provide me with a legal and secure way to return these materials to them. While writing a memoir about my experiences at CIA, CIA’s Publication Review Board never provided me with a secure manner to deliver my manuscript, instead demanding I send potentially classified materials via my Gmail account. CIA emailing me to inform me that something I had submitted via Gmail for pre-publication review was classified became routine. Keep in mind, CIA’s emails always came after what they claimed was classified information had already been compromised. Why was the information compromised? Because CIA had directed me to send documents containing potentially classified information to them in an unsecure manner, most commonly via Gmail. CIA has continued to rebuff my requests to set up a more secure means to communicate. When my Chromebook with a copy of my memoir was stolen from my hotel room in Paris on Christmas Day in 2014, CIA refused my entreaties to speak to them about an obvious security breach. A month later, CIA would write me at my address in Spain, informing me significant portions of my memoir was classified. Whoever stole my computer, by CIA’s own admission, had gained access to significant amounts of classified information. But to CIA, this was a non-issue.
After CIA informed me that I had classified information at my overseas residence, their Security Officers directed me to return it to them via international mail for destruction. In keeping with CIA’s total disregard for anything related to information security, there was a problem with CIA’s proposal. Namely, placing classified material in the mail, international or domestic, is illegal because it is not a secure means to transport sensitive material and risks exposing classified material to our adversaries. When I refused to comply with their unlawful order, CIA Security Officers berated me, including James in CIA’s Security Operations Center (SOC), who identified himself as CIA management, calling me a hypocrite for refusing to violate US espionage laws. James also invoked the name of CIA’s Director of Support, Jeanne C. Tisinger, saying she had personally approved me shipping classified documents via an international carrier.
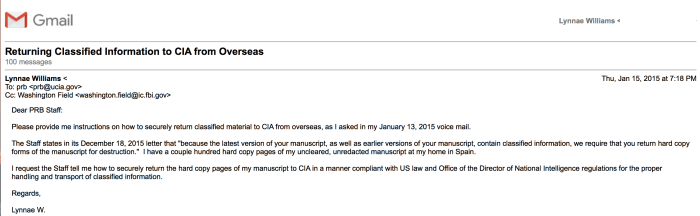


I have digital recordings of my interactions with staff in the SOC and other CIA support personnel. I began making these recordings in response to the extraordinary ways in which they were ordering me to mishandle classified material. The fact that I was able to digitally record CIA Officers making incriminating statements, speaks volumes to their unawareness of basic OPSEC. I could write a book on the OPSEC failures I have lived through dealing with CIA personnel, a book that would shock the conscience of anyone familiar with the basic countermeasures necessary to protect highly sensitive intelligence information. With all of this background, upon reflection, the shock I initially experienced upon learning of CIA’s historic counterespionage failure was unwarranted. The real surprise is given CIA’s sloppy approach to OPSEC, this counterespionage disaster did not occur sooner.
My experience is not an isolated incident, over the years there have been several widely reported cases of CIA’s inability to protect highly sensitive material. In 2011, CIA compromised the identity of several of its agents reporting on Iran by using poor OPSEC while allegedly conducting meetings at a Pizza Hut in Lebanon. These spies were CIA agents targeting Iran and Hizbollah.
[urlpreviewbox url=”http://abcnews.go.com/Blotter/cia-spies-caught-fear-execution-middle-east/story?id=14994428″/]
CIA’s poor OPSEC also led the Italians to detect the Agency’s illegal rendition of one of their residents, Abu Omar, a Muslim Cleric in Milan. What led the Italian’s back to CIA? CIA’s poor OPSEC. CIA Operations Officers used their cell phones and credit cards in a manner that allowed Italian authorities to systematically unmask their identities.
[urlpreviewbox url=”https://www.wired.com/2007/06/st-cia/”/]
As someone whom CIA labeled “paranoid,” “delusional,” and “psychotic,” for attempting to follow basic security procedures, although I was initially surprised by CIA’s monumental loss of highly classified materials related to its Cyber Intelligence program, in retrospect, I certainly understand how it happened. Julian Assange’s analysis of CIA’s breathtaking loss of classified information is dead-on when he says, “This is an historic act of devestating incompetence to have created such an arsenal and stored it all in one place and not secured it.”
How the CIA built a vast cyberweapons arsenal–and then lost control of it https://t.co/K7wFTdlC82 #Vault7 pic.twitter.com/06BKihmHwn
— WikiLeaks (@wikileaks) March 7, 2017
The most damning part of Wikileaks massive disclosure was not CIA’s hacking capabilities, (although to the general public, it understandably is…) but the fact that someone was able to exfiltrate this amount of information from CIA’s protected network, under the nose of CIA’s Office of Security and counterespionage personnel. Anyone who has worked in intelligence knew CIA had an advanced ability to hack into our electronic devices, we can assume the Chinese, Russians and other sophisticated intelligence services do as well, which is why OPSEC has always been fundamental to the effective operation of intelligence services worldwide. Since leaving CIA, I have always assumed the US government and/or other actors have compromised my computers and other devices, and acted accordingly. The documents released by Wikileaks show CIA was doing exactly what we would expect them to do: researching, developing and refining methods to go after their worldwide targets. During an interview in 2012, then CIA Director David Petraeus explained the Agency’s goals with regards to our everyday electronics, saying, “Items of interest will be located, identified, monitored, and remotely controlled through technologies such as radio-frequency identification, sensor networks, tiny embedded servers, and energy harvesters — all connected to the next-generation internet using abundant, low-cost, and high-power computing.” What we have today, is confirmation that many of the things Petraeus alluded to in 2012, and much more, have become a reality at Langley.
[urlpreviewbox url=”https://www.wired.com/2012/03/petraeus-tv-remote/”/]
The real story here is how CIA lost control of such a significant amount of information and why post- Edward Snowden (Snowden as we know him would not exist had CIA not granted him a clearance, handing him the keys to the Intelligence Community kingdom), CIA is still relying on the same antiquated security procedures for vetting current and prospective employees and securing its information. Why hasn’t CIA caught up with 21st century technology? I knew CIA was at risk based on my personal experience with CIA Security Officers who did not have a basic grasp of OPSEC, Information Security or Information Technology. During the intervening years, I have written to the Federal Bureau of Investigation, the chairmans of the Senate Select Committee on Intelligence and the House Permanent Select Committee on Intelligence, and many others about CIA’s untenable OPSEC posture. My warnings have fallen on deaf ears…and today, CIA is confronted with ostensibly the largest loss of sensitive intelligence in its history.
Will CIA reform its security apparatus? I will be surprised if it does. I am tempted to laugh and say, “I told you so.”…I must admit, I am relishing the pure, unadulterated schadenfreude of this moment. After all CIA put me through, I deserve it. At the same time, as a former intelligence professional, I understand the importance of secret intelligence to the preservation of our democracy. The Intelligence Community cannot sustain these continued losses and remain effective. The question remains, when will the Intelligence Community begin to take security reform seriously? If it continues along the same path, these losses will occur with increased frequency, as would be “copycat” leakers are emboldened by others’ successes, creating a cascade effect. CIA can do amazing things with technology, nevertheless, CIA’s adversaries can undermine CIA in amazing ways using that same technology. On March 7, 2017, CIA’s defenses suffered a stunning defeat at the hands of a formidable asymmetric adversary, Wikileaks. Only time will tell if CIA is willing to do what is needed to recover from this devastating and unprecedented loss. CIA and the entire Intelligence Community would do well to heed the words of Cicero as they move forward following the latest catastrophic attack from within.



